Create a new app integration.
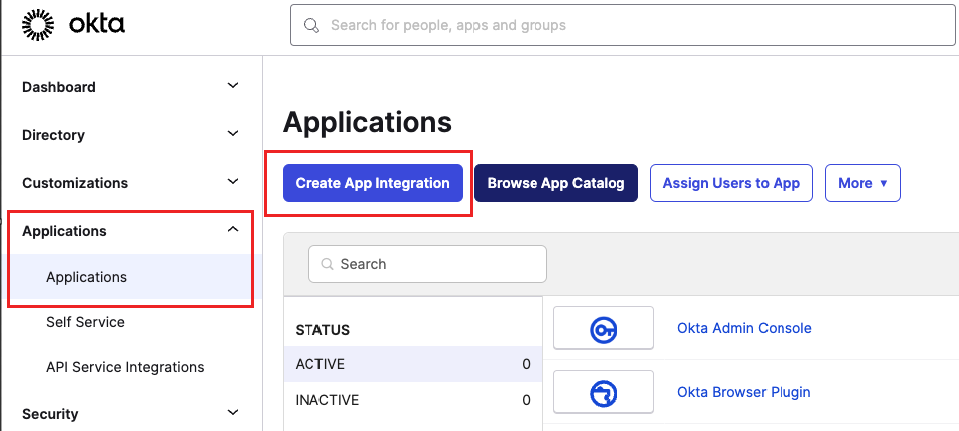
- Go to Applications and click Create App Integration.
- On the Create a new app integration page:
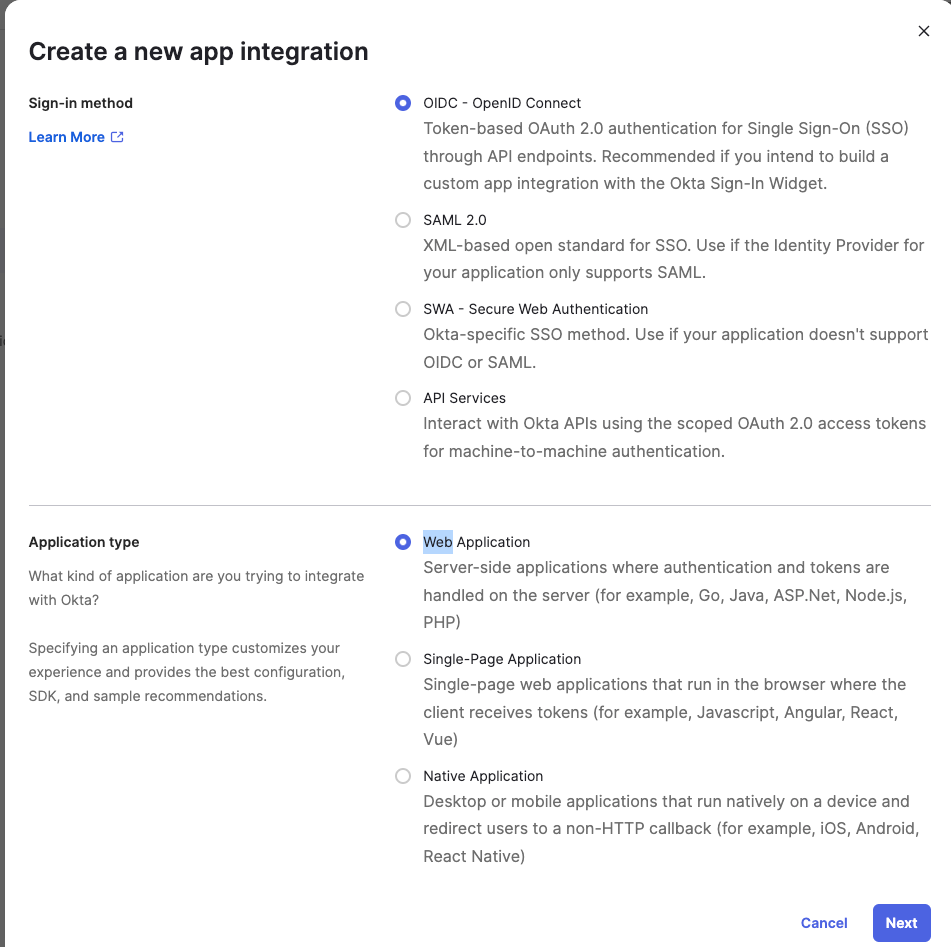
- Select Sign-in method - OIDC - OpenID Connect
- Select Application Type - Web Application
- Click Next
- Enter the App Integration name as OpenMethods-OIDC
- Grant Type
- Select Authorization code, Refresh Token and Implicit
- Sign-in redirect URIs
- Sign-out redirect URIs
-
Assignments
-
Control Access
- Select Skip group assignment for now
-
Control Access
- Click Save.
 |
 |
PKCE Verification
-
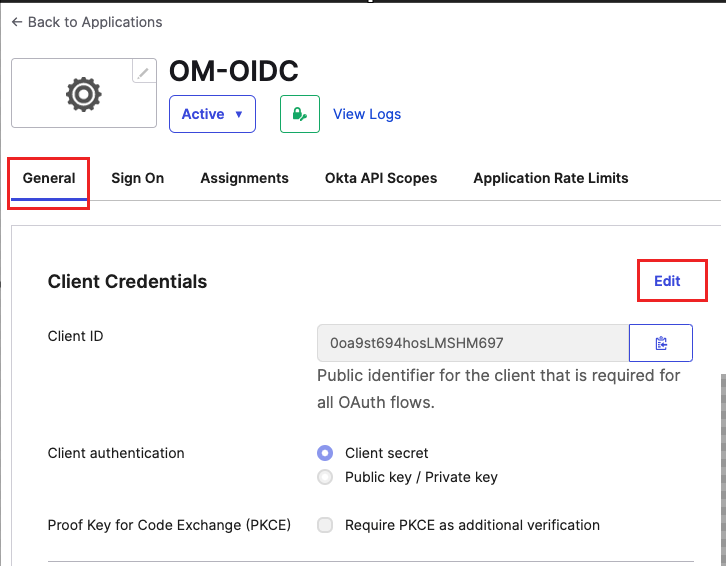
Select the Application and click General
- Click Edit under Client Credentials
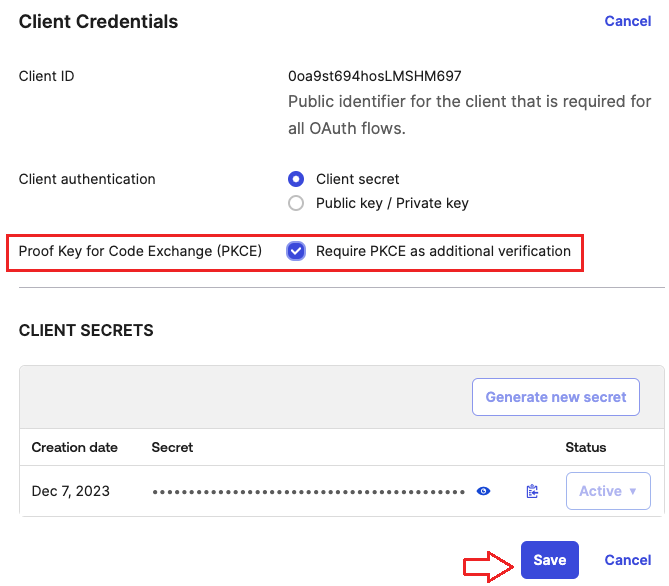
- Select Require PKCE as additional verification
- Click the Save button.
 |
 |
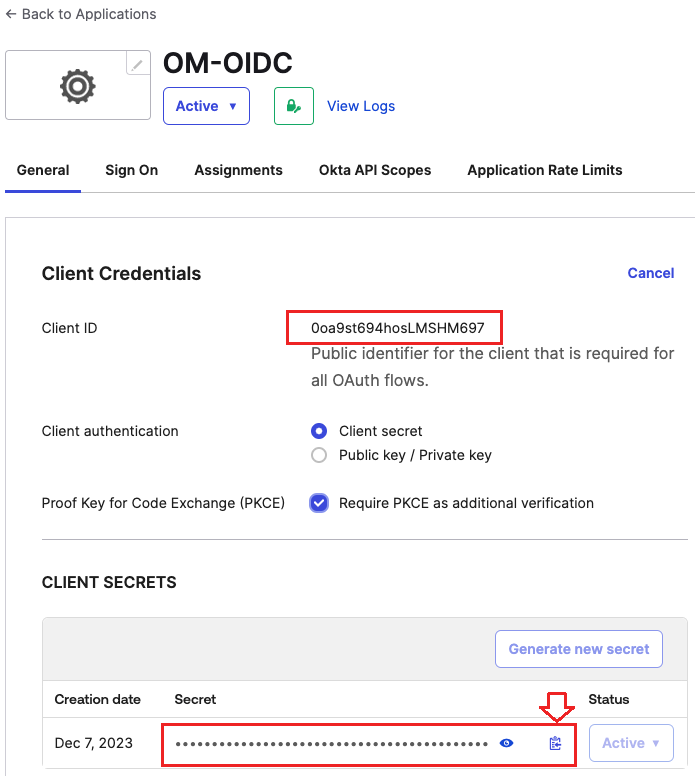
Copy the required values.
- Select the Application
- Click the General tab
- Copy the Client ID
- Copy the Secret.
- Replace <Base URL> in the following URLs, and both URLs will be used in the OpenMethods Experience Designer Provider configuration .
- Authorize Endpoint: https://<Base URL>/oauth2/v1/authorize
- Token Endpoint: https://<Base URL>/oauth2/v1/token
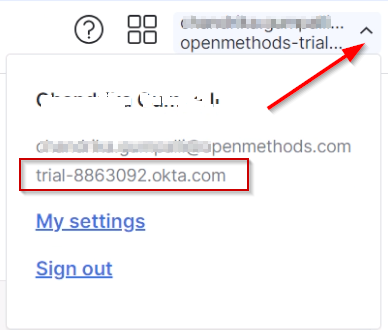
- Base URLs can be obtained by clicking the arrow in the top right section and copying the URL as highlighted in the image.
Assignments
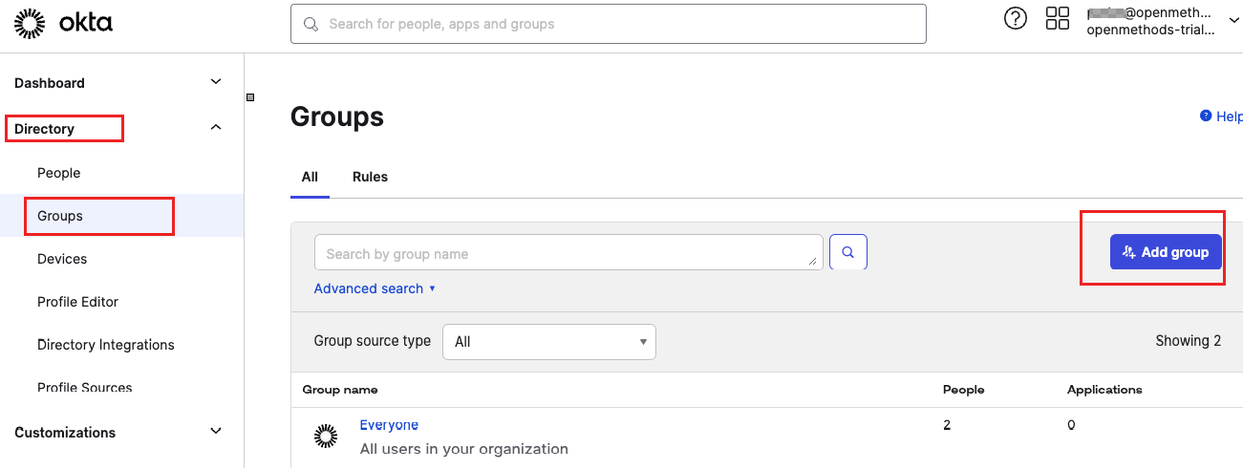
- Create a new Group
- Click Directory and Groups, and then click the Add Group button.
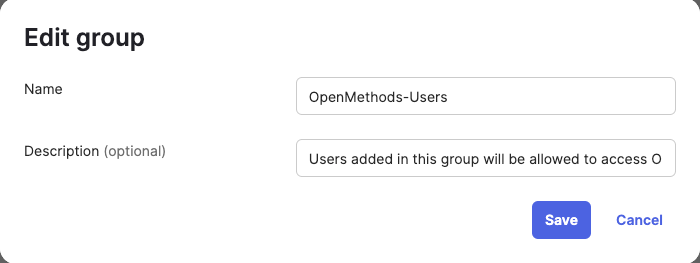
- Enter the name OpenMethods-Users.
 |
 |
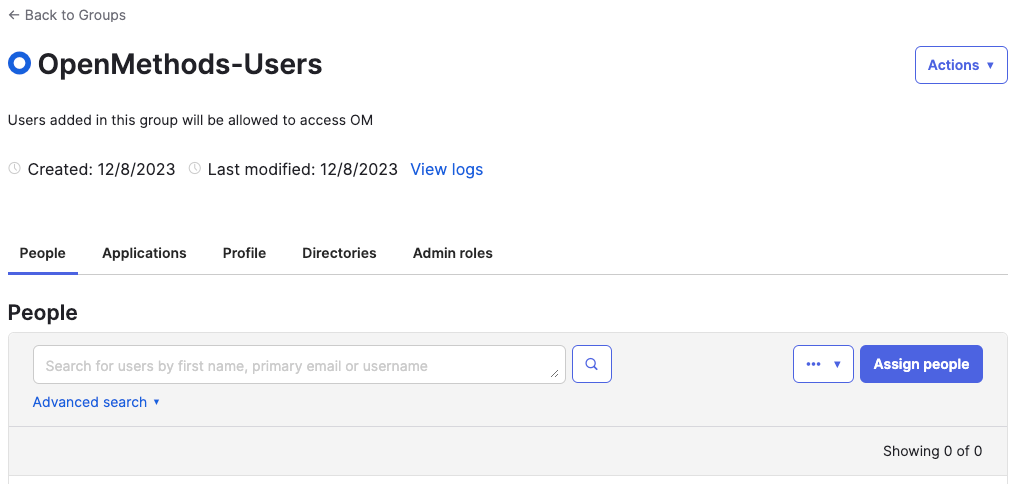
- Assign people to the Group.
- Click the group name OpenMethods-Users from the Group's list
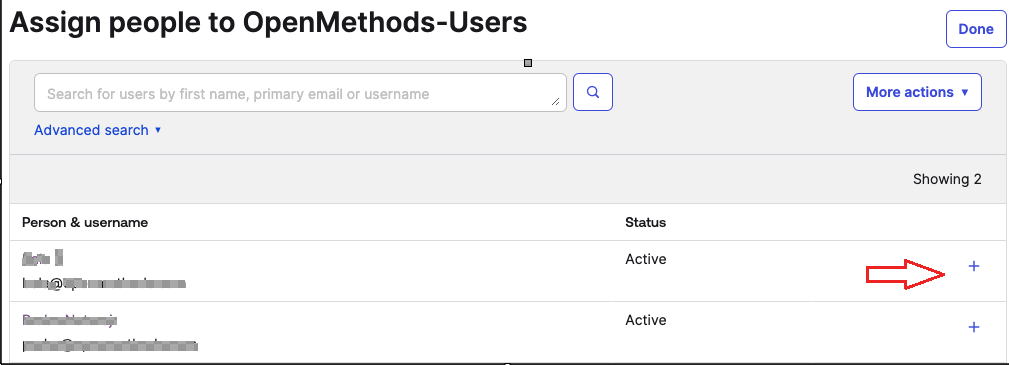
- Click the Assign People button
- Click the + sign to select the people from the list, by clicking the + sign, who should be added to the Group.
 |
 |
- Assign the Group
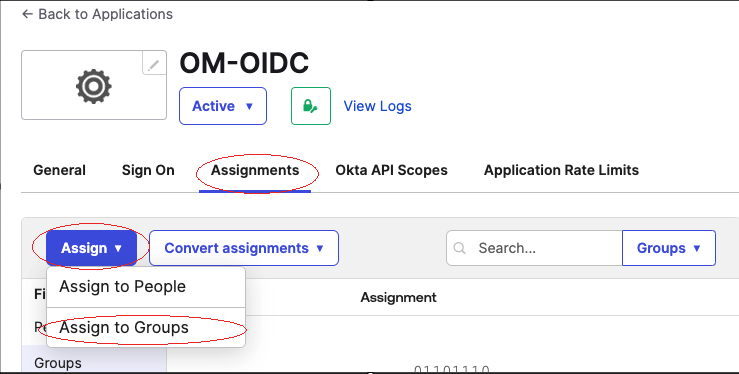
- Goto Applications and Select the Application name
- Click Assignments
- Select Group from the Assign dropdown
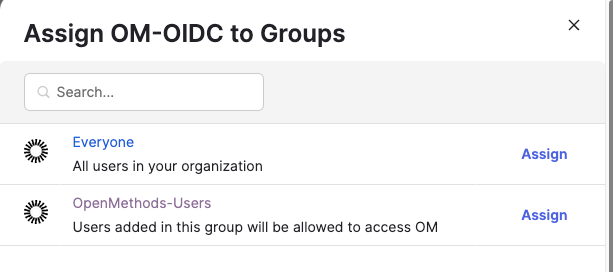
- Click Assign to Groups
- Click Assign next to the OpenMethods-Users Group
- Click the Done button.
 |
 |