Add Application
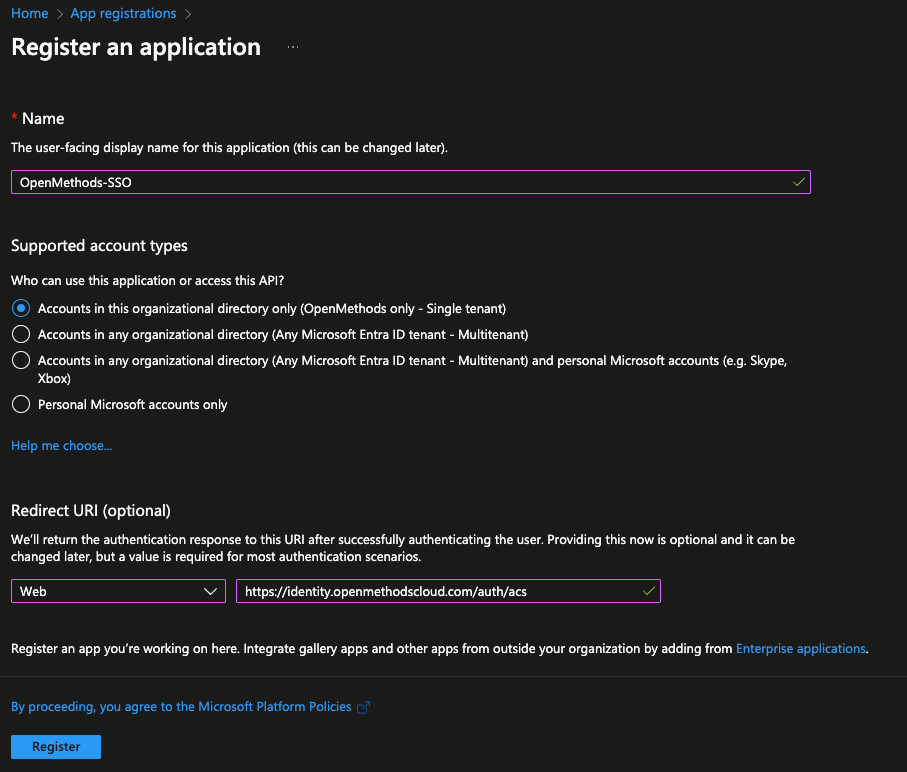
- Click the App Registration located under the Azure Services.

- Click New Registration
- Enter Name - The suggested name is OpenMethods-SSO
- Select the appropriate account types.
- Redirect URI
- Select Web
- Enter https://identity.openmethodscloud.com/auth/
- Click the Register button.
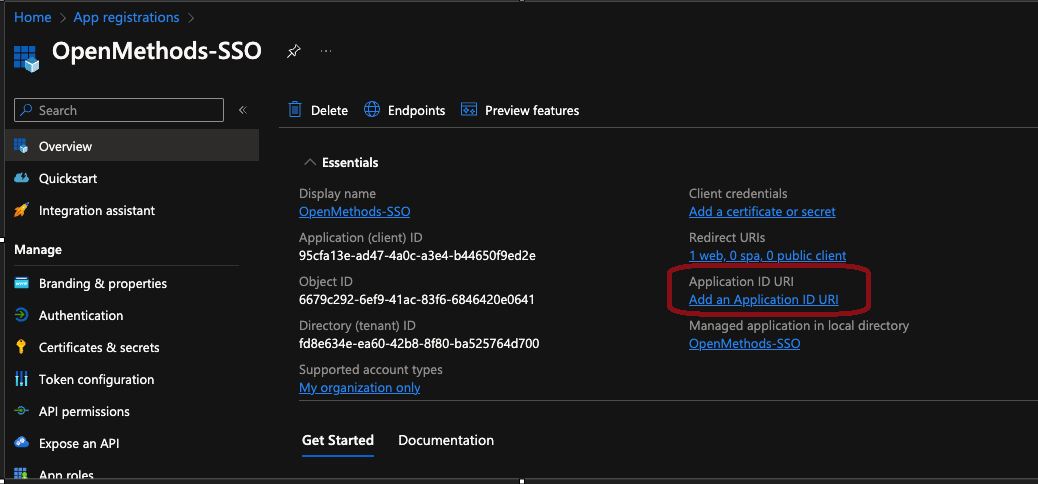
- Click Add an Application ID URI
- Enter OpenMethods-APPS-SSO or any desired value.
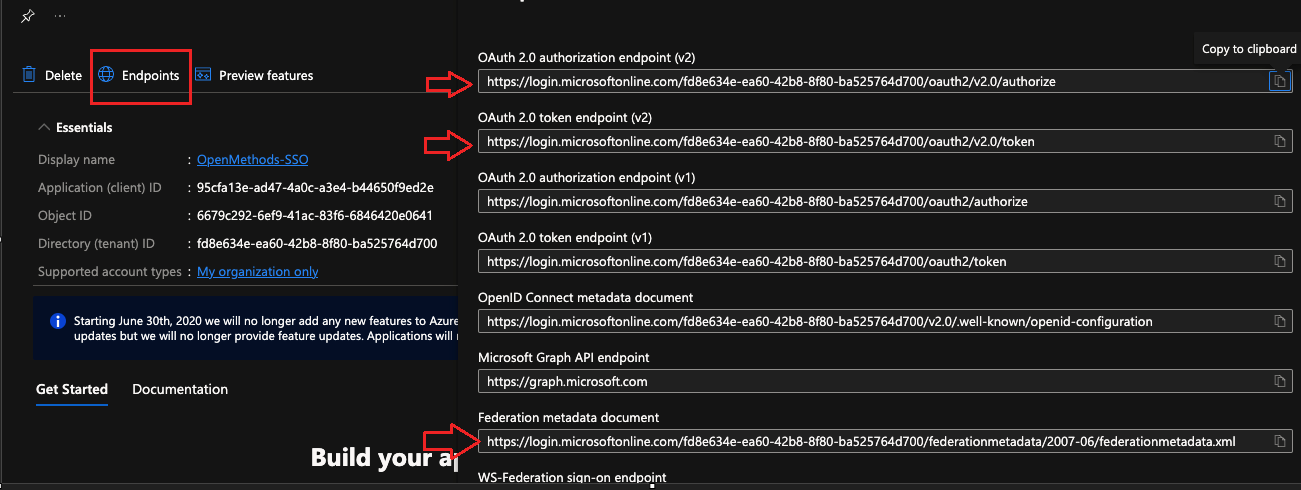
Copy the required values
- Click Endpoints link
- Copy the following URLs:
- OAuth 2.0 authorization endpoint (v2)
- OAuth 2.0 token endpoint (v2)
- Federation metadata document
- The metadata URL is used to configure SAML2 as IdP.
- Client ID
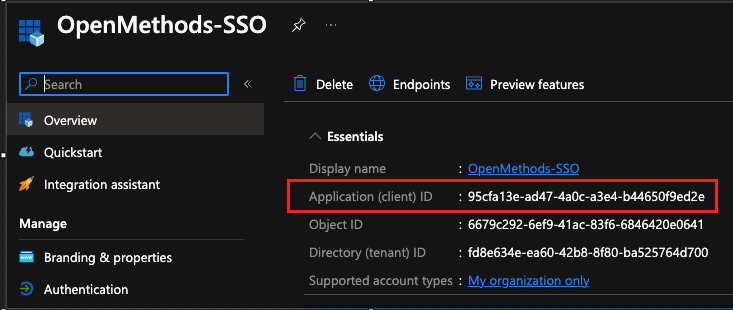
- Click Overview
- Copy the Application (client) ID
- Client Secret
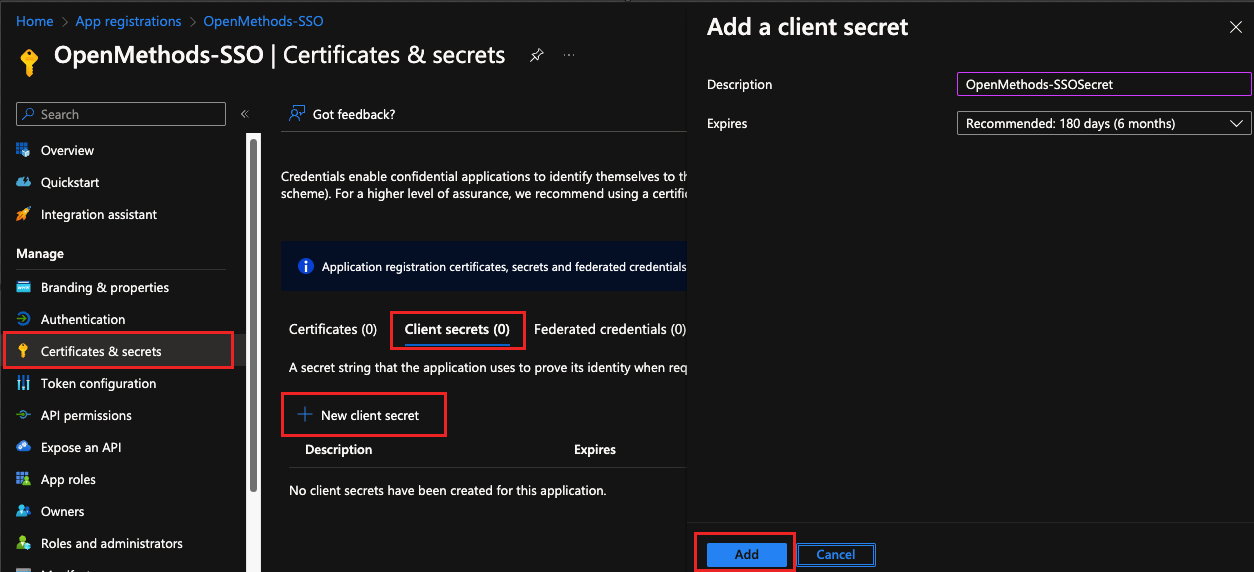
- In the application overview page, navigate to the Certificate & secrets section.
- Under the Client Secrets tab, click the New Client Secret.
- Enter the proper description, like OpenMethods-SSO-Secret.
- Choose the Expiration duration from the drop-down
- Click the Add button.
-
Important to Remember:
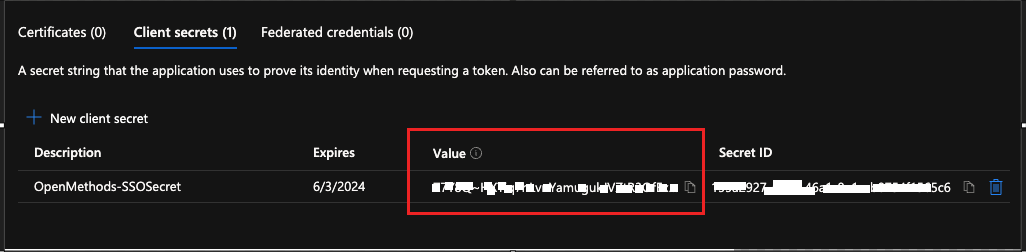
- Once the secret is generated, make sure to note it down (the Value) immediately, as it will not be visible again.
- Note down the Expiration date.
- Re-create the secret before it expires and update the new secret in the SSO configuration in OpenMethods Experience Designer.
- Copy the Secret Value
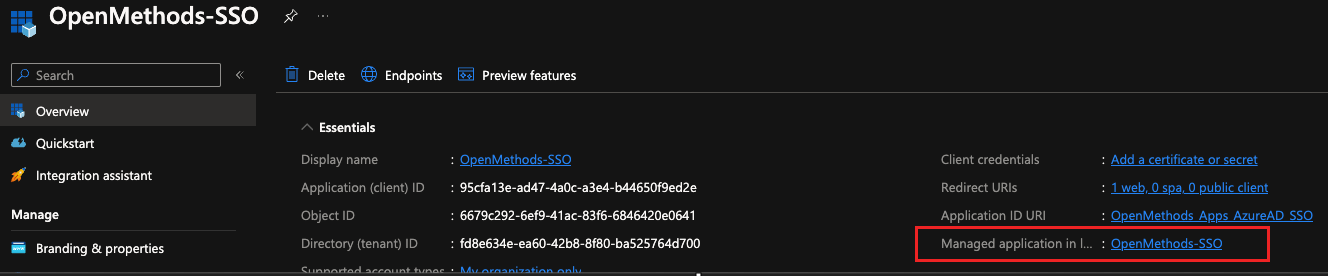
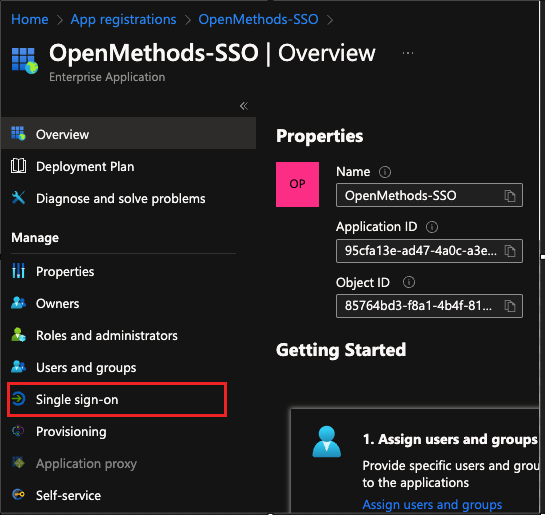
- Click the Managed Application.
- Click the Single sign-on.
-
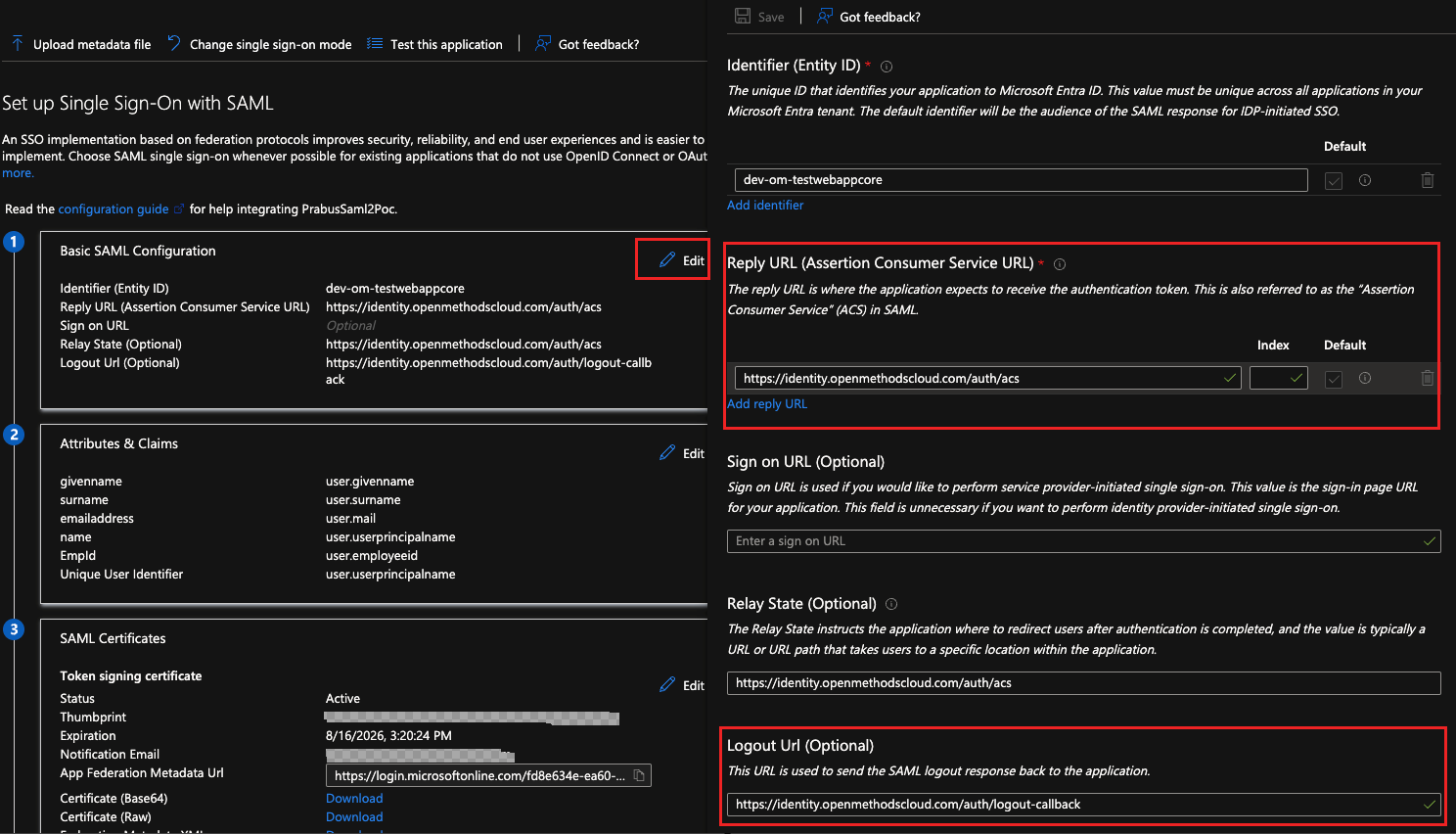
Client Edit under the Basic SAML configuration
- Enter the reply URL https://identity.openmethodscloud.com/auth/acs
- Select Default
- Enter the Logout URL https://identity.openmethodscloud.com/auth/logou-callback
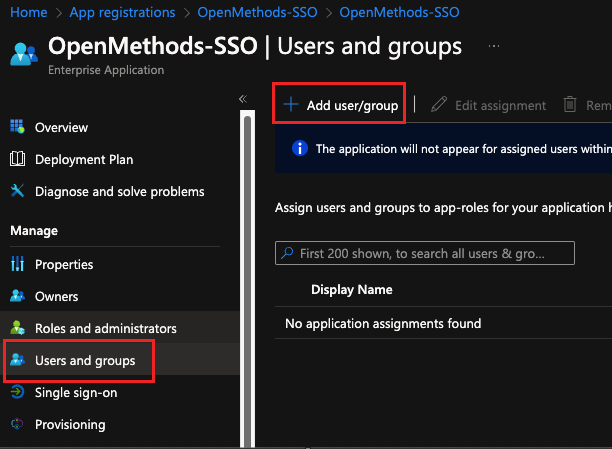
ADD USERS
- Click Overview
- Click Users and Groups located Under Manage Application.
- Follow the steps involved in the user selection.
- Selected users will be assigned to the Application.