OpenMethods allows users to log in with a single sign-on (SSO) system using SAML 2.0.
An identity provider (IDP) that supports SAML 2.0 can be set up in various ways, such as a self-hosted Active Directory Federation Services (ADFS) server. ADFS is a Microsoft service that provides web login using existing Active Directory credentials.
This guide uses screenshots from Windows Server 2019 and AD FS Management Version: 10.0.0.0, but you should be able to perform similar steps on other versions.
To begin, you need to install ADFS on your server. However, the installation and configuration of ADFS are beyond the scope of this guide. You can find detailed information about it in this Microsoft article.
During testing, ensure that your workstation authentication is set to the same test email you use for the test. Otherwise, ADFS will not allow you to log in, even if the configuration and profile are correct.
💡 We strongly recommend configuring SSO in your browser's separate incognito mode window. This way, you can keep the session in the standard window, allowing you to switch off the SSO authorization in case of a misconfiguration.
Values required for the OpenMethods SSO Provider Configuration
-
Client Id
- The Client Identifier value is copied from the following instruction
-
Client Secret
- The Shared Secret value from the following instruction.
-
Authorization URL
- https://<ADFS Server domain>/adfs/oauth2/authorize
-
Token URL
- https://<ADFS Server domain>/adfs/oauth2/token
-
Sign Out URL
- https://<ADFS Server domain>/adfs/oauth2/logout
Add Application
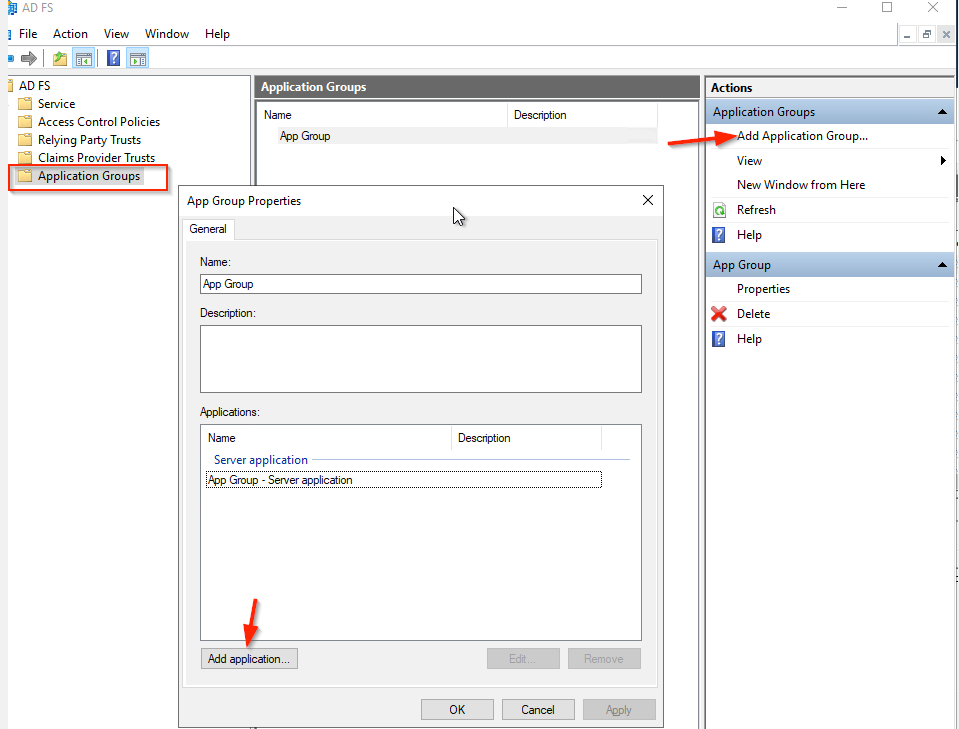
- Open the AD FS Management Console
- Click Application Groups
- Click Add Application Group
- Add Application Group first. If the Application Group is not already added, then.
- Click Add Application
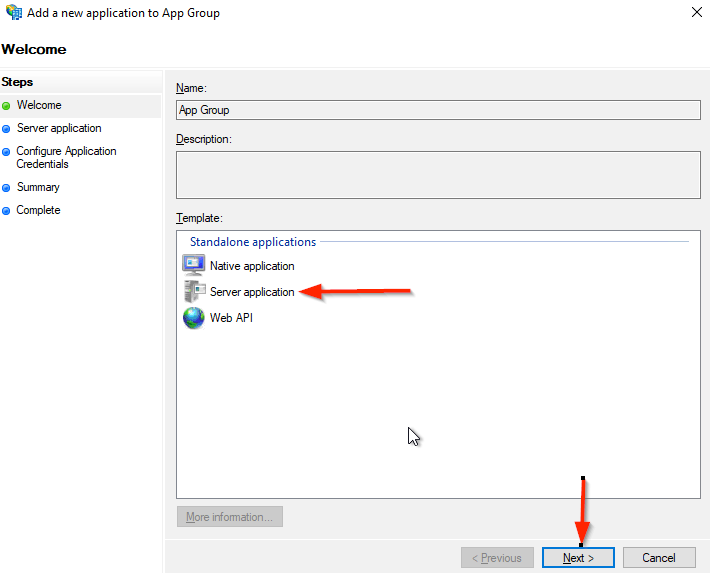
- Select Server Application
- Click the Next button.
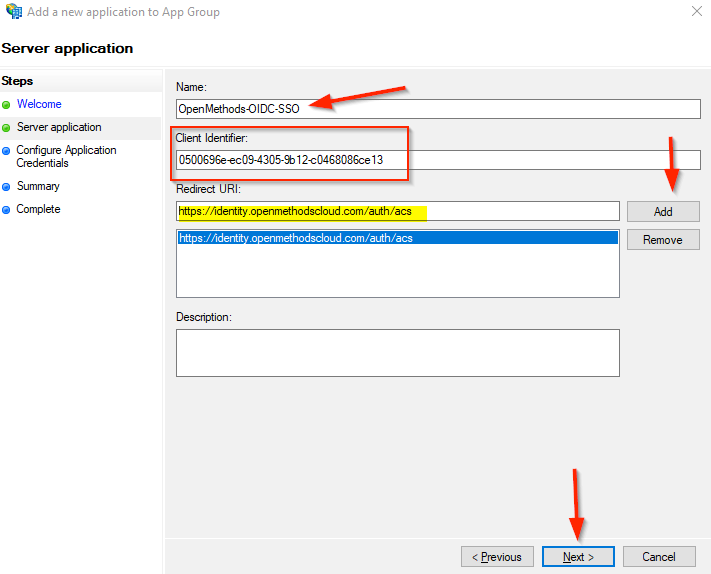
- Enter the Name; the suggested name is OpenMethods-OIDC-SSO.
- Enter the Redirect URI - https://identity.openmethodscloud.com/auth/acs
- Click Add button
- Copy the Client Identifier
- We will add this to the OpenMethods SSO Provider Configuration page
- Click the Next button.
- Select Generate a shared secret.
- Click Copy to the clipboard
- We will add this to the OpenMethods SSO Provider Configuration page.
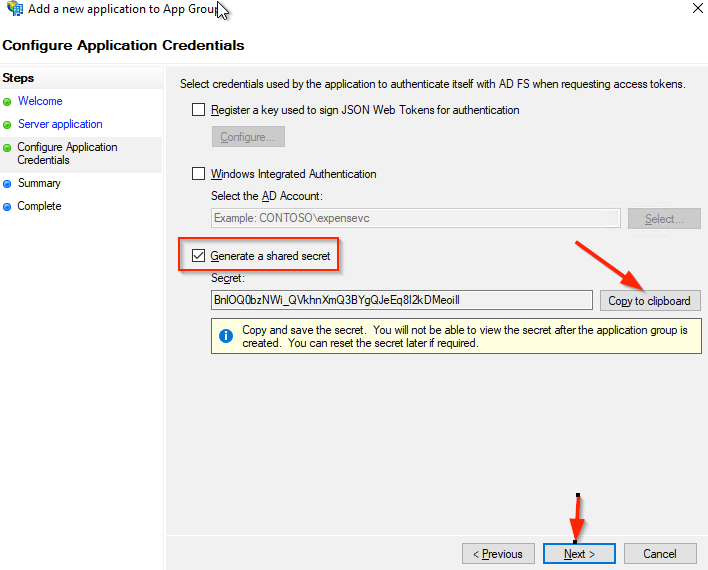
- Click Next button
- Close the Application wizard.